Authenticate User Process
Content
- Overview
- reCAPTCHA
- Process Flow
- App Settings
- User Journey Flow Diagram
- API Walkthroughs
- Error Codes
- Revision History
Overview
This Process defines how a user signs into ULM Cloud. This is a straightforward operation with additional options for additional user verification (e.g., two-factor authentication, reCAPTCHA).
Note: This Process operates differently from most other Processes, in that it is not started by the usual Start Process API (but from its own dedicated endpoint), and requires a mandatory payload in the request body.
reCAPTCHA
ULM Processes that involve authentication include support for reCAPTCHA, which is one of many different types of CAPTCHA. CAPTCHA is an automated, dynamically-generated challenge that the user must pass in order to proceed with authentication. These challenges are simple and easy for humans to pass, but difficult for malicious automated "bots" to bypass.
There are multiple types and versions of CAPTCHA, the criteria for when and how to challenge a user is dependent on the CAPTCHA type. For example, some versions prompt the user to click a checkbox, and prove they aren't a malicious bot, after a failed number of login-requests.
In other cases, the system instead requires the user to match images to further validate their identity.

By default, ULM Cloud supports Invisible reCAPTCHA, version 2. This version includes an "invisible" check that monitors multiple factors in the user's behaviour before making any kind of prompt.
Support for more CAPTCHA and challenge types (e.g. 2FA, honeypot) are roadmapped for future release.
Process Flow
This flow describes the standard Authenticate User Process from a high-level, "happy path" flow.
| Authenticate User Process | |||
|---|---|---|---|
| Actors | Front-end user, Client Application, ULM Cloud | ||
| Pre-Conditions | The front-end user has a ULM User ID with at least one verified authN ID (email or mobile). | ||
| The user is currently anonymous (i.e., they are not authenticated in ULM). | |||
| Basic Flow | 1 | The user navigates to the client application, enters their authN ID and password, and then clicks Sign In. | |
| 2 | The process consumes and validates the user's credentials, and checks the user's current status. | ||
| Notes: - All ULM user IDs are stored in the cloud as ULM User data entities. - A given user's authN IDs are registered and stored as attributes on the corresponding ULM User entity. - A user ID and its authN IDs each have a status. The Process checks these statuses during sign-on. - If the authN ID has an activating status, the user has onboarded but hasn't verified their email/mobile. - If the authN ID has a pending status, they are replacing an email/mobile, but haven't verified the new one. - If the user attempts to login with an unverified email/mobile, the Process simply resends an action token to that external channel for verification, and then ends without authenticating the user. - ULM does allow users to register a non-verifiable authN IDs as unique "alias," and the Authenticate User Process does accept aliases for sign-in. However, the user must have at least one verified email/mobile before they can register an alias. |
|||
| 3 | |||
| 3a | (Conditional) ULM prompts the user to pass a reCAPTCHA check/challenge, if enabled. | ||
| Notes: - The Enable reCaptcha app setting includes configuration points for the client secret keys. - By default, The Authenticate User Process supports Invisible reCAPTCHA, version 2. - Google determines when to silently check/challenge the user. |
|||
| 3b | The user passes the reCAPTCHA check, and the Process continues. | ||
| 4 | The Process opens a user session. | ||
| Post-Conditions | The user is now authenticated in ULM Cloud. | ||
| Error Conditions | Reached the maximum number of failed authentication attempts. | ||
| The User profile is currently locked. | |||
| User ID (and or the authN ID) is not yet verified. | |||
| Generic authentication required error for the following scenarios: | |||
| a | Invalid or unknown authentication identifier. | ||
| b | User not found in ULM. | ||
Authentication with Social Media
ULM also supports the option for a user to authenticate using a social media account that is associated to their ULM User ID. See the Onboard and Authenticate User with Social Account Process, Authentication Flow for more information.
App Settings
Certain aspects of the Process' behaviour are controlled by configurable application settings.
| Application Settings | Default Setting | |
|---|---|---|
| Max failed sign-in attempts | The maximum number of times the Process accepts bad input before locking the user out. | 10 |
| Count failed attempts within | The length of time in which the user's total failed attempts are counted towards lockout, measured in seconds. After this time expires, the count resets. | 3600 |
| User lockout duration | The length of time that a user ID lockout lasts, measured in sections. | 3600 |
| Enable reCAPTCHA | Determines whether or not reCAPTCHA, v1 is enabled. This app setting include multiple fields for client and test secret keys. | Enabled |
| tokenURL | Base for the action token URL to include in the notification message sent to the user's external channel. The actual token value will be appended to this String to form the complete URL. This app setting is applicable for when a user attempts to sign-in with an unverified email/mobile. When this occurs, the Process sends the token out to that email/mobile for verification. |
https://idp/user_confirm?token_value= |
| Token (long-form) Expiration | Determines the number of minutes before a verification link expires. | 10080 minutes (7 days) |
| Token (short-form) Expiration | Determines the number of minutes before a short OTP expires. This setting is not configurable, and is simply noted here for context. |
5 minutes |
Note: All app settings are set within the MarketONE ULM Admin web application.
User Journey Flow Diagram
This diagram illustrates the standard user journey using the Authenticate Process.
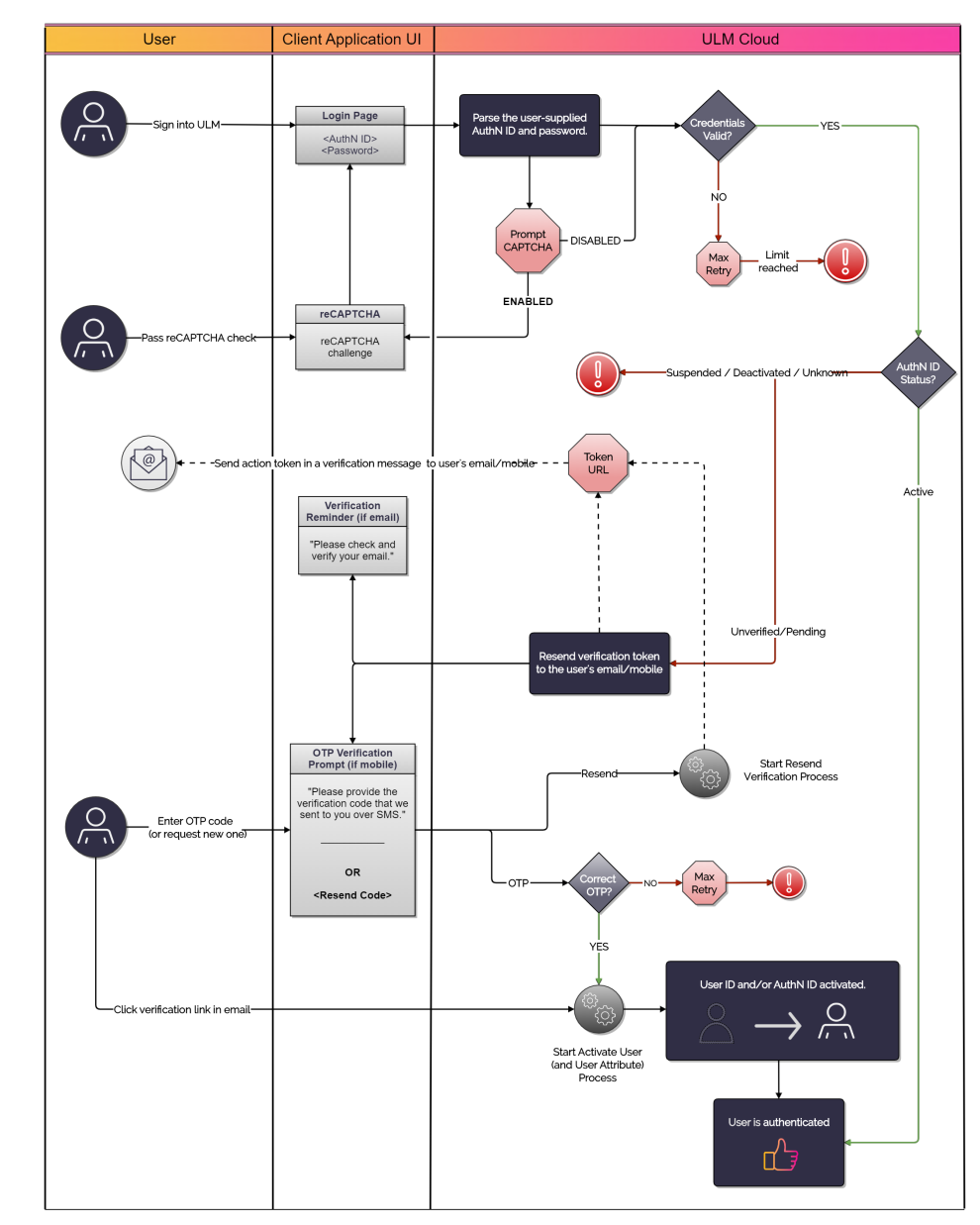
This diagram also incorporates best practice routes to the Resend Verification and Activate User Processes.
API Walkthroughs
The following section provides guided walkthroughs of the Authenticate User Process, including demonstrations of the various branching paths the Process can take during its execution.
Basic Authentication Scenario
This is the simplest flow for the Authenticate User process. The Process consumes a valid authN ID and credential, and successfully authenticates the user. The Process then returns a successful response that indicates the user has been authenticated to ULM, and can proceed to make requests to protected APIs.
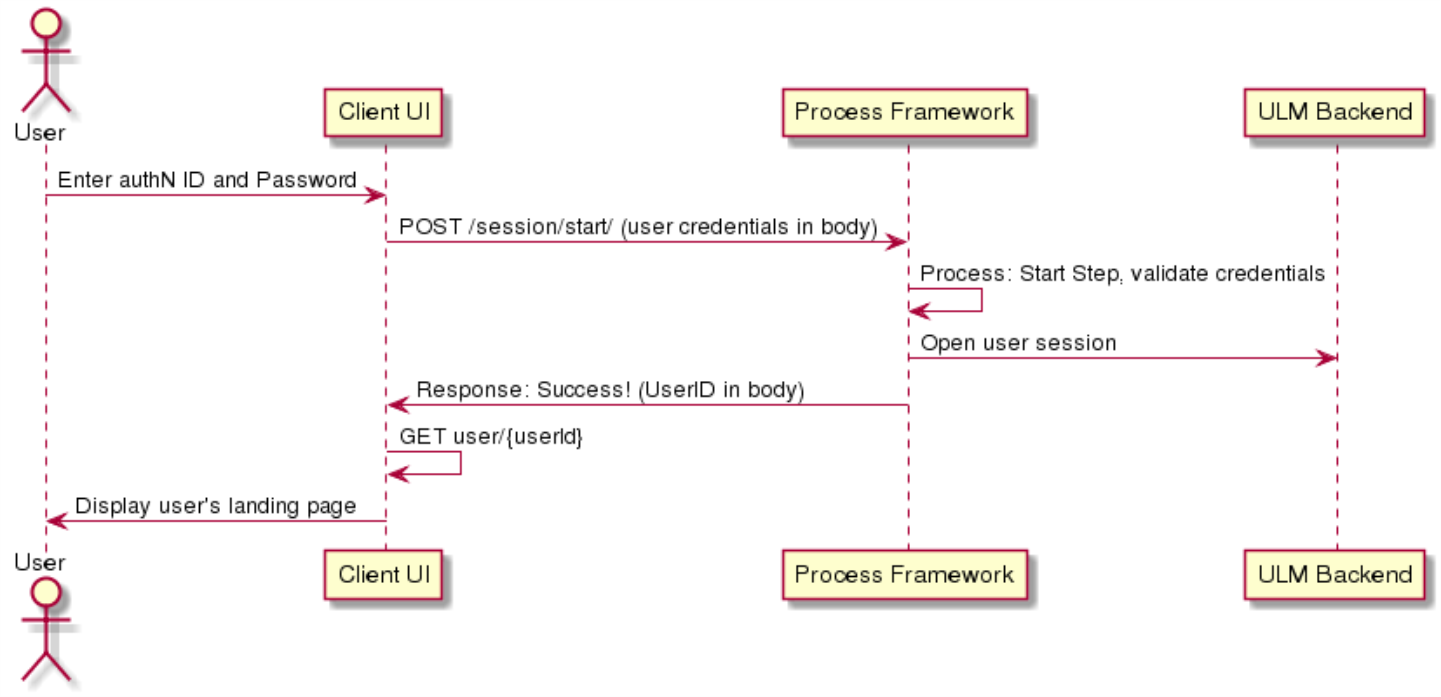
Initial Request
The Session Start API initializes the Process:
| POST /session/start |
|---|
{
"authnIdentifier": "father@operator.com",
"credential": "letmein"
}
|
Request Parameters
| Parameter | Description |
|---|---|
| authnIdentifier | The user's registered email address, mobile number, or alias (if any). |
| credential | The user's password. |
Response
If the user provides valid credentials, and no other authentication protocols are necessary (e.g., 2FA) then the Process responds with an HTTP 200 status code, and user details in the body:
| Response Body |
|---|
{
"processId": "eec918ff-5db4-4fee-a601-5ff76a099c8e",
"lastStep": true,
"runtimeId": 229,
"userId": 12345,
"userAuthenticated:" true
}
|
Response Parameters
| Parameter | Description |
|---|---|
| processId | The unique identifier for this instance of the Process. |
| lastStep | Boolean that indicates whether or not this was the last step in the Process. |
| runtimeId | Identifier of the ULM Runtime entity currently associated to the ULM User entity. About Runtime Entities: Upon user creation or authentication, ULM Cloud looks for a JRUNTIMEID cookie in the end user's browser or application. If no cookie is found, ULM creates a Runtime Entity with a unique ID and associates it to the user during the login phase. ULM will generate and pass a corresponding JRUNTIMEID cookie for clients to store and return with subsequent requests. |
| userId | The unique identifier of the current user. |
| userAuthenticated | Boolean that indicates if the user was authenticated into ULM. |
The client application can retain the user and runtime IDs to use MarketONE's ULM APIs to perform CRUD operations against those ULM entities.
Unverified Email/Mobile Response
If the user tries to authenticate with an unverified email or mobile, the Process simply resends an action token to that external channel, and then ends.
| Response Body (from unverified authN ID) |
|---|
{
"processId": "21d31975-583c-4ad5-aa3b-909386545032",
"output": {
"pkat": "d022a6c1-cc00-40f8-b5f2-74b03c7e5a61"
},
"lastStep": true
}
|
Any Process step that results in the sending of a ULM action token also returns a corresponding pkat to the client application. The client application should retain this information to render user options on the UI to trigger either the Activate User and/or Resend Verification Message Processes as needed.
Response Parameters
| Parameter | Description | |
|---|---|---|
| processId | The unique identifier for this instance of the Process. | |
| output | Object containing additional data that the client can retrain and use for additional operations beyond the Process. | |
| pkat | Unique Proof Key for Action Token that accompanies a tokenId, if any. See Action Tokens for more details. | |
| lastStep | Boolean that indicates whether or not this was the last step in the Process. | |
Basic Authentication Scenario with Invalid Credentials
This example repeats the basic scenario above, but includes bad user input in the first request.
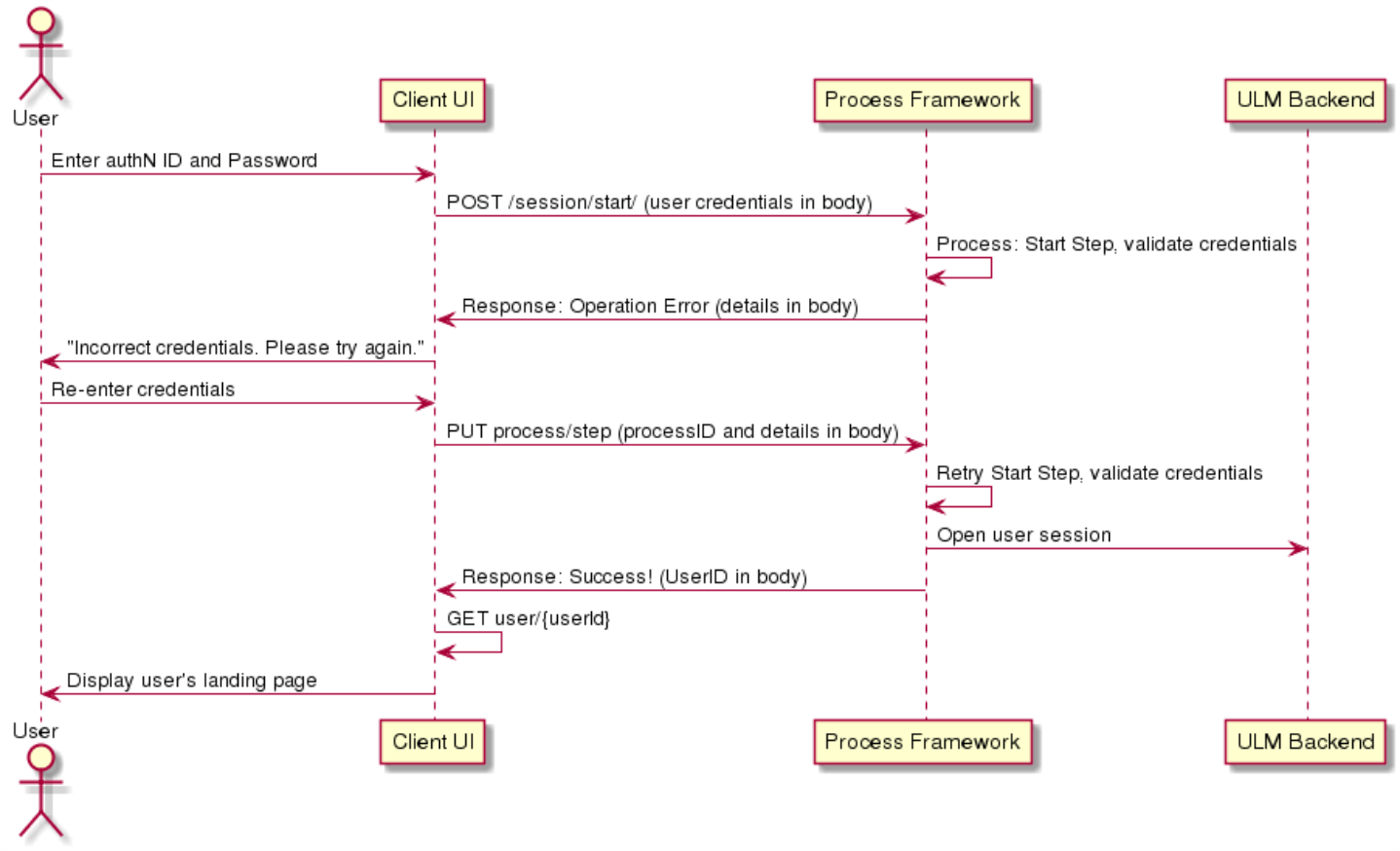
Initial Request
The Session Start API initializes the Process:
| POST /session/start |
|---|
{
"authnIdentifier": "father@operator.com",
"credential": "LetMeIn"
}
|
Request Parameters
| Parameter | Description |
|---|---|
| authnIdentifier | The user's registered email address, mobile number, or alias (if any). |
| credential | The user's password. |
Response: Operation Error
If the user provides invalid credentials, the Process responds with an HTTP 401 status code. The body includes an operationError array with the reason(s) as to what went wrong:
| Response Body |
|---|
{
"processId": "49819a56-5b81-49a0-8d26-2b39d7ce3859",
"stepName": "StartStep",
"operationError": [
{
"code": "authentication-required",
"type": "com.uxpsystems.mint.framework.ulm.process.exception.LoginFailureException",
"message": "Bad credentials"
}
],
"lastStep": false,
"lastFailedStepAction": {
"processId": "49819a56-5b81-49a0-8d26-2b39d7ce3859",
"stepName": "ReEnterPrompt",
"parameters": {
"authnIdentifier": "String",
"credential": "String"
}
}
}
|
Response Parameters
| Parameter | Description | |
|---|---|---|
| processId | The unique identifier for this instance of the Process. | |
| stepName | The internal name of the step that the Process is currently on / just executed. | |
| lastStep | Boolean that indicates whether or not this was the last step in the Process. | |
| operationError | Array of possible error object. Each object describes a separate error condition. | |
| code | An error object's internal code name. | |
| type | Internal reference of the operation error type. | |
| message | Optional message that describes the error in plain readable language. | |
| lastFailedStepAction | Object that repeats the previous Process step's details and required input. This allows the client to essential retry the failed request. | |
Re-Request: Fixed Credentials
Using the Process Step API, the client retries the request again with correct user credentials:
| PUT /process/step |
|---|
{
"processId": "49819a56-5b81-49a0-8d26-2b39d7ce3859",
"Parameters": {
"authnIdentifier": "father@operator.com",
"credential": "letmein"
}
}
|
Request Parameters
| Parameter | Description | |
|---|---|---|
| processID | The unique identifier for this instance of the Process. | |
| parameters | Object that contains the data requested in the previous Process response. | |
| authnIdentifier | The user's registered email address, mobile number, or alias (if any). | |
| credential | The user's password. | |
Response: Successful
If the credentials have been validated successfully on this attempt, the API will respond indicating authentication is successful, as in the previous example:
| Response Body |
|---|
{
"processId": "49819a56-5b81-49a0-8d26-2b39d7ce3859",
"lastStep": true,
"runtimeId": 5049,
"userId": 1,
"userAuthenticated": true
}
|
Response Parameters
| Parameter | Description |
|---|---|
| processId | The unique identifier for this instance of the Process. |
| lastStep | Boolean that indicates whether or not this was the last step in the Process. |
| runtimeId | Identifier of the ULM Runtime entity currently associated to the ULM User entity. |
| userId | The unique ULM identifier of the current user. |
| userAuthenticated | Boolean that indicates if the user was authenticated into ULM. |
The client application can retain the user and runtime IDs to use MarketONE's ULM APIs to perform CRUD operations (e.g. GET /user/{userId}) against those entities.
About Max Retries: Each Process accepts a limited numbers of user input retry attempts before temporarily locking the user out, to avoid brute-force password attacks. If the limit is reached, the API will return this:
| Response Body |
|---|
{
"processId": "49819a56-5b81-49a0-8d26-2b39d7ce3859",
"stepName": "ReEnterPrompt",
"operationError": [
{
"code": "user-profile-locked",
"type": "com.uxpsystems.mint.framework.ulm.process.service.ServiceStep.GeneralFailure",
"message": "Your User profile has been disabled, Please try later"
}
],
"lastStep": false
}
|
The Max failed sign-in attempts app setting controls failed attempt limit. The default setting is 10 failed attempts. This setting is configured in the MarketONE User Admin web application.
Basic Authentication Scenario with reCAPTCHA
reCAPTCHA is a service provided by Google, and is integrated into a website through JavaScript code provided by Google themselves, with ULM accepting a verification token from reCAPTCHA (which ULM can independently verify through back-channel requests to reCAPTCHA APIs).
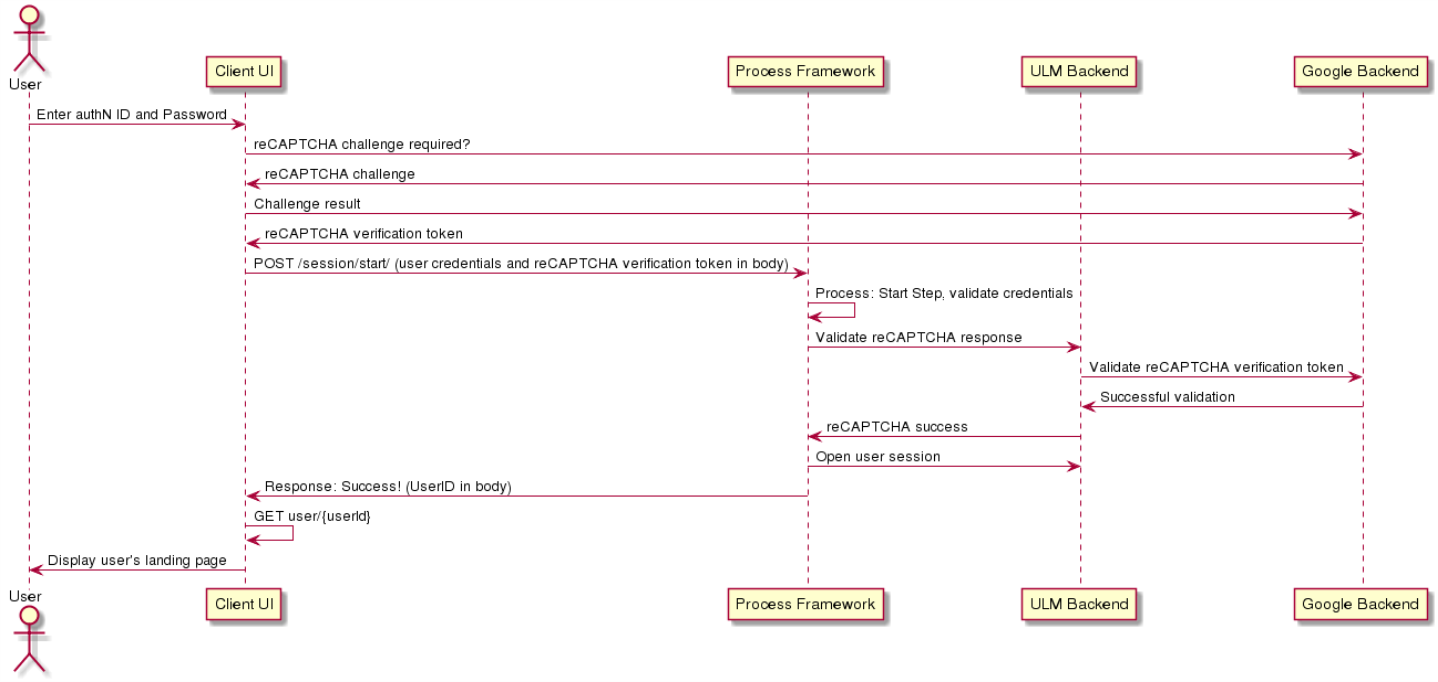
Request: Provide Credentials and reCAPTCHA Verification Token
The Session Start API initializes the Process, and the reCAPTCHA verification token is included as an additional field alongside the user's standard credentials.
| POST /session/start |
|---|
{
"authnIdentifier": "father@operator.com",
"credential": "letmein",
"recaptchaResponse": "any random value"
}
|
Request Parameters
| Parameter | Description |
|---|---|
| authNIdentifier | The user's registered email address, mobile number, or alias (if any). |
| credential | The user's password. |
| recaptchaResponse | The verification token provided by reCAPTCHA either after a challenge has been completed, or reCAPTCHA has implicitly verified the user as human (without any challenge required). ULM Cloud will use this token to independently verify with Google that reCAPTCHA has been successfully completed during the login process. |
Response: Success
The API will respond as normal, returning a successful authentication response if the credentials provided alongside the reCAPTCHA verification token are valid:
| Response Body |
|---|
{
"processId": "eec918ff-5db4-4fee-a601-5ff76a099c8e",
"lastStep": true,
"runtimeId": 229,
"userId": 1,
"userAuthenticated"
}
|
Response Parameters
| Parameter | Description |
|---|---|
| processId | The unique identifier for this instance of the Process. |
| lastStep | Boolean that indicates whether or not this was the last step in the Process. |
| runtimeId | Identifier of the ULM Runtime entity currently associated to the ULM User entity.
About Runtime Entities: Upon user creation or authentication, ULM Cloud looks for a JRUNTIMEID cookie in the end user's browser or application. If no cookie is found, ULM creates a Runtime Entity with a unique ID and associates it to the user during the login phase. ULM will generate and pass a corresponding JRUNTIMEID cookie for clients to store and return with subsequent requests. |
| userId | The unique identifier of the current user. |
| userAuthenticated | Boolean that indicates if the user was authenticated into ULM. |
Note: The client application can retain the user and runtime IDs to use the MarketONE ULM APIs to perform CRUD operations against those entities.
Error Codes
Below is a comprehensive list of potential error codes that may be returned during the execution of this Process.
Common Error Codes
ULM Core Process - Common Process Error Codes
Process Specific Error Codes
| HTTP Status | ULM Error Code | Description |
|---|---|---|
| 401 | user-profile-locked | The user's profile is locked. |
| 401 | authentication-required | One or more of the below is true: - Authentication identifier is not valid - Credential (password) is not valid - User not found - reCAPTCHA verification code is not valid |
| 401 | user-activating | The authentication identifier provided is in an activating status. This Process only allows authentication with activated (i.e., verified) authentication identifiers. |
| 401 | invalid-code | The Process prompted the user for a 2FA code, but the provided code was invalid. |
Revision History
| Version | Description |
|---|---|
| 2020.09 | Added this topic. |